Account administrators can enable SAML single sign-on (SSO) ![[External link]](https://paligoapp-cdn-eu1.s3.eu-west-1.amazonaws.com/impact/attachments/f01cdffa431a4d75ff09c130b66974d4-b8ebe06c75d53cc8d24756ae9b7589e2.svg)
SAML SSO uses a connection for impact.com with your identity provider. impact.com currently supports the following providers:
Enable SAML SSO
Before starting, make sure you have your IDP metadata file in .XML format handy — this file needs to be uploaded to impact.com.
From the top navigation bar, select
[User profile] → Settings.
In the left column, under General, select Account User Authentication.
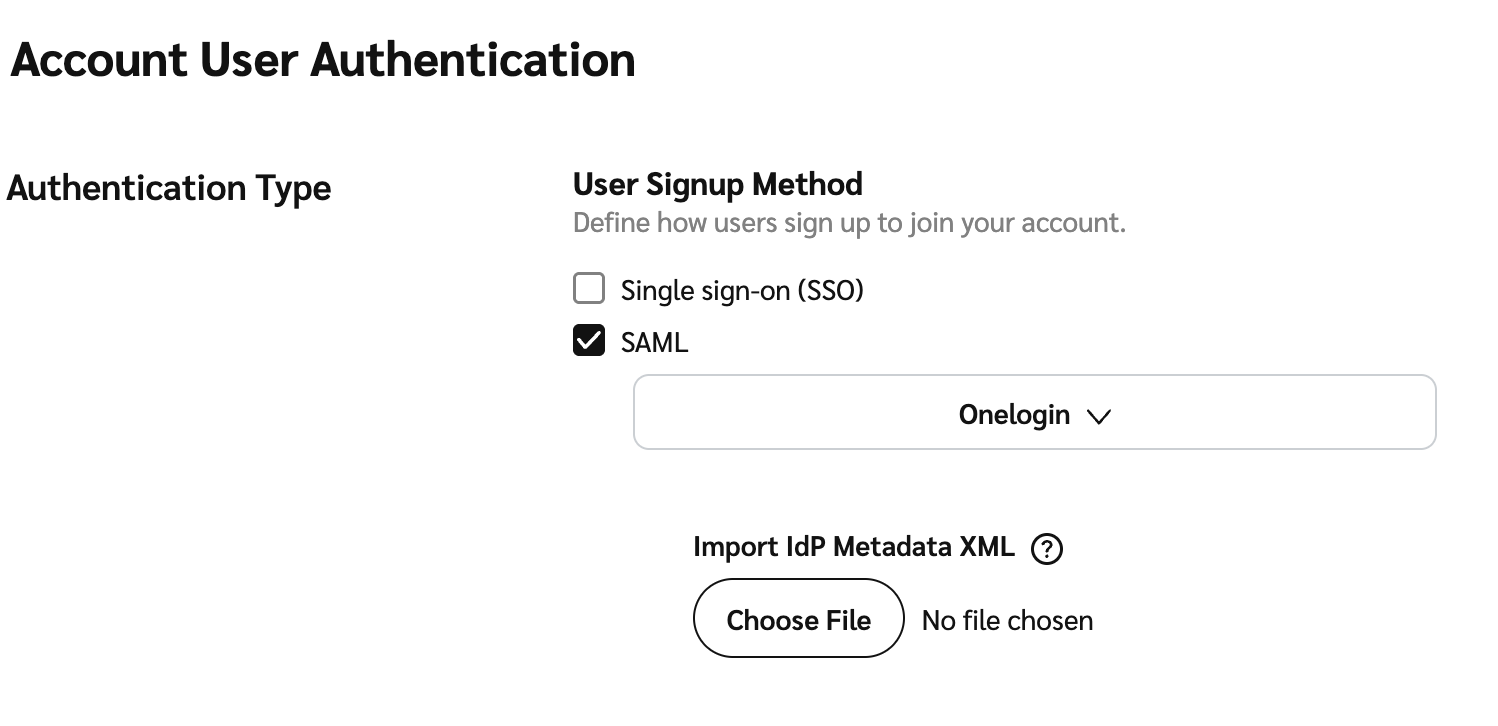
Next to the Authentication type line item, select
[Check box] SAML and use the
[Drop-down menu] to select your identity provider.
Use the file picker to find and upload your .XML metadata file.
At the bottom of the screen, select Save.
The following instructions need to be completed for each individual user that will use SAML SSO:
From the top navigation bar, select
[User profile] → Settings.
In the left column, go to General and select Account Users.
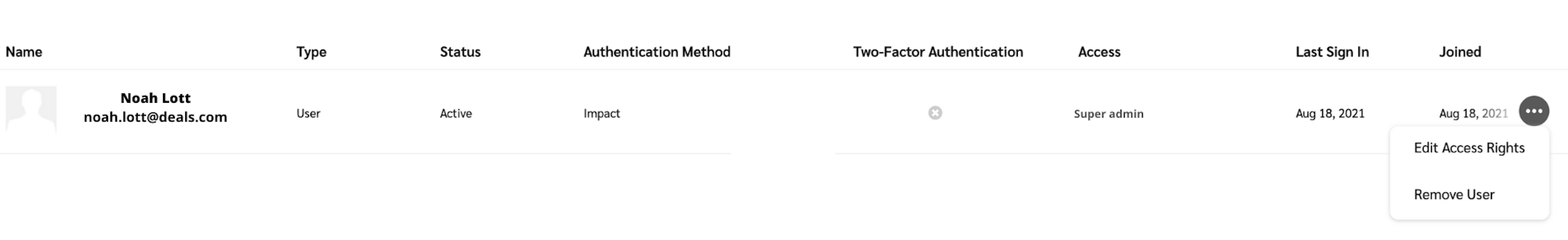
Hover your cursor over a user and select
[More] → Edit Access Rights
In the User Signup Method section, select SAML.
At the bottom of the slide-out, select Save.
There are 2 ways for users to access impact.com with SAML SSO:
Through your identity provider (IDP) — Configure a connection/connector in your IDP and use it to sign users in.
Through your brand’s unique login link — For users who do not sign in via the IDP connection.
OneLogin — In OneLogin, find the Impact Partnership Cloud connection in the OneLogin App Catalog and follow the on-screen instructions to enable and configure the app.
ADFS, Okta, & Microsoft Entra ID — Create a new custom connection with these exact values:
Field
Value to input
Single Sign On URL / Reply URL / ACS URL
https://app.impact.com/saml/SSO
Recipient URL
https://app.impact.com/saml/SSO
Destination URL
https://app.impact.com/saml/SSO
Audience Restriction
https://app.impact.com
Name ID Format
EmailAddress
Response
Signed
Assertion Signature
Signed
Signature Algorithm
RSA_SHA1
Digest Signature
SHA1
Assertion Encryption
Unencrypted
SAML Single Logout
Disabled
AuthnContextClassRef
PasswordProtectedTransport
Microsoft Entra ID — Create a new custom connection with these exact values:
Field
Value to input
Reply URL (Assertion Consumer Service URL)
https://app.impact.com/saml/SSO
Reply URL (implicitly)
https://app.impact.com/saml/SSO
Identifier (Entity ID)
https://app.impact.com
Name identifier format (Advanced Settings → “Name identifier format”)
EmailAddress
Response Signing Option (Sign SAML response)
Signed
Sign SAML Assertion (option)
Signed
Signing Algorithm
RSA_SHA1
Digest Algorithm
SHA1
Encryption Certificate (optional)
Unencrypted
Single Logout URL
Disabled
Default AuthnContextClassRef (not exposed directly)
PasswordProtectedTransport
If a user is not signing in via your IDP, they can use a unique branded login link to access your impact.com account. To get this login link:
From the top navigation bar, select
[User profile] → Settings.
In the left column, under Branding, select Advertiser Login Branding.
Your branded link will look similar to this:
https://app.impact.com/abe/Stark-Industries12345678912345/login.user?preview=t
From the Login Link field, copy & save the Login Link to distribute to your impact.com account members.